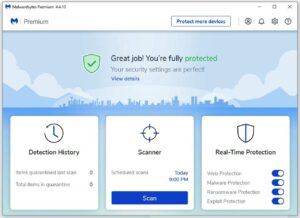
Your personal computer or whatever computing devices you use at home are an underrated aspect of homeownership. After all, from your computer, you may control smart appliances, home alarms and cameras, solar installations, and even your financials like your bank accounts, credit cards, loans, utilities, and more! So imagine how vulnerable all these things are if your computer ends up being compromised by malware and/or viruses, which open the door to hackers or other bad actors hijacking your life! That’s where MalwareBytes comes into the picture, and in this review, I go over my experiences spanning over 5 years with this software.
What Is The Difference Between Malware and Viruses?
To make a long story short, malware is a generalized catch-all term encompassing any type of malicious software.
A virus is a specific class of malware that replicates itself (just like real viruses do). However, in the digital space, it does its thing by attaching or injecting code to programs that then activate upon execution.
Both the terms malware and virus are used interchangeably, and I suspect this is the case because antivirus and anti-malware / antimalware programs (MalwareBytes was considered the latter) have pretty much converged in terms of the protection services offered over the years. You could even argue that the only difference between the companies that claim to be antivirus versus anti malware pretty much comes down to branding!
In the past, antivirus companies targeted only viruses while antimalware companies, which were newer to the game, targeted the stuff that antivirus companies didn’t catch or target in their detection schemes.
Viruses are known to delete or encrypt files as well as modify the behavior of applications or even get into the operating system and disable various (critical) functions. Heck, some have been capable of even reformatting a drive!
My first personal experience with viruses happened back in the late 80s when my 486 PC was infected with the keypress virus. What would happen was that I type or enter a keystroke (normally for playing games but it could also be when writing a report in a word processor), and then the virus would suddenly replicate a particular keystroke hundreds (maybe thousands of times).
It got so bad that depending on what was going on with the computer, those spontaneous keystrokes would cause the computer to crash or hang.
So I became sensitized to the possibility of computer viruses and ultimately malware since that time, but over the years, they’ve become quite sophisticated so countermeasures have also evolved accordingly.
In addition to computer viruses, other forms of malware include:
- Worms – a standalone self-replicating program exploiting a vulnerability in the system (which is why you want to stay up-to-date with security updates on the software you use)
- Ransomware – encrypts critical files while demanding a ransom to be paid to the perpetrator to do the decryption (provided they’re true to their word)
- Scareware – tries to frighten victims through pop-ups or banners indicating infection and then funneling them into buying software (typically that they don’t need) or providing financial data
- Adware – pushes unwanted advertisements via pop-ups and banners regardless of whether it involves a web browser or without one (in which case an underlying process is being used instead)
- Spyware – secretly skims or collects information about the user, including website browsing history (though Google toes this line) as well as applying a keylogger. Keyloggers are particular insidious because they record and reveal user keystrokes so it can be used to reveal passwords, credit card and/or bank account info, usernames, and more
- Memory-resident or Fileless Malware – hides in a trusted application or tool (e.g. Microsoft Excel web tools or files) and operates in the computer’s memory so it can evade detection or avoid triggering security alerts. Such malware may activate despite the user not clicking the offending file to activate it.
What Is MalwareBytes?
MalwareBytes is a company that started off as anti-malware software to be used to supplement existing antivirus software. However, over time, they’ve sought to de-mystify the field of cybersecurity through their user-interface offerings as well as through user-education.
In fact, this is how I discovered them when I suspected something was wrong with my computer and my antivirus software (which was Kapersky at the time) couldn’t detect and disinfect it. MalwareBytes pulled me through that drama, and I’ve been using them ever since.
Like with antivirus software, they primarily detect malware and once found, they then quarantine or delete them (what to do is up to the user).
Although they have a free version, I paid for their premium version so I could get real-time protection, protect multiple machines, and take advantage of scheduled full scans. The full scans take a bit longer (think hours) than the typical quick scans that only take a few minutes.
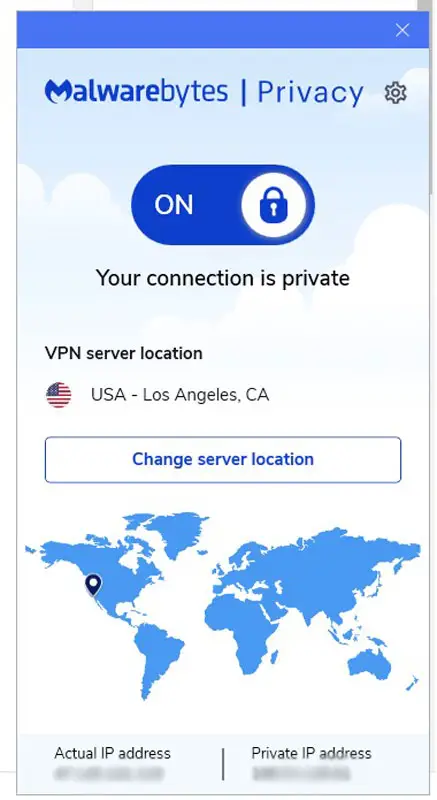
Since about 2018, MalwareBytes has made updates to become more of an all-in-one anti malware / antivirus solution, including providing an add-on paid virtual private network (VPN) service called MalwareBytes Privacy.
They have also added BrowserGuard, which is supposed to intercept you from clicking on websites and links flagged to contain malware or have a bad reputation concerning phishing, political and/or conspiracy actors, and scams.
Why Use MalwareBytes Premium?
The following are the main reasons why I’ve continued to maintain my subscription through their premium and privacy plus plan.
Simple Interface and Fast, Accurate Scanning
One thing I appreciate about MalwareBytes is its simple interface. Although it has a lot of complex controls (most of which you probably don’t want to mess with unless instructed to), its out-of-the-box configuration has been pretty sufficient for my needs. This means, it does quick scanning while its default multi-layered approach has been pretty accurate in my experiences.
Based in USA
Speaking of best-effort and intent, MalwareBytes is based out of the USA. Thus, I have some degree of confidence that political or state-sanctioned spying or unwanted snooping from say Russia, other parts of Eastern Europe, India, and/or China isn’t being done through this software.
Real-time Protection Didn’t Slow Down My Machine
MalwareByte’s real-time run-in-the-background detection (which is not available in the free trial version) also doesn’t seem to intrude or impact my computer’s performance over the years that I’ve been using them. I’ve had some antivirus software slow down my machine to a crawl, which is why I’m particularly sensitive to this.
Offers Privacy Protection Through VPN
As of 2018, I also started to use their Privacy solution (which costs about $20 more than their typical premium plan). This is basically a Virtual Private Network (VPN) that changes (thereby anonymizes) my IP address while also encrypting the traffic over that network so no one can snoop my traffic nor try to geolocate me.
How Have I Been Using MalwareBytes Premium?
Just to give you an idea of how I use MalwareBytes in my day-to-day computing tasks (where I spend a lot of time working on websites like this one), I pretty much let both the real-time protection and VPN run at start-up. This means that the protection software is pretty much always on whenever I am on my computer, and I let it take care of say the 80% of the cases while investing no more than 20% of the resources.
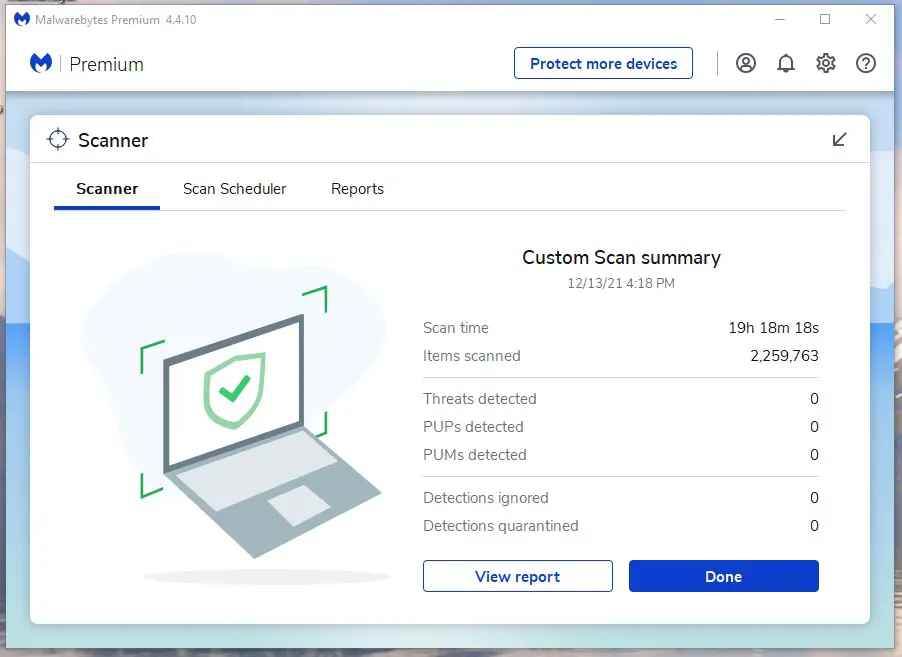
Then, I run a deep, full scan once a week on Sunday nights where I’d leave the computer on overnight and throughout Monday to let the software do its thing. This job tends to be resource intensive and takes several hours, which is why I’m willing to eat the additional electricity bill to let MalwareBytes do its thing during this time when I’m typically not actively using the computer.
But by letting the automated quick scans as well as real-time protections do their thing daily in conjunction with running the weekly full scans, I feel like I pretty much have minimized my risk exposure to things that have fallen through the cracks.
Of course, I can also do my part as a user by engaging in best practices of hard passwords, not clicking on bad links, bad attachments, or suspicious websites in general, and not falling for social engineering hacks. I view MalwareBytes’ role in the grand security scheme to help me if I do click a bad link or download a bad attachment (let’s face it, no one is perfect and you never know what a member of the family might do on your computer). That said, I’d much rather do what I can to not make the software work harder than it needs to (and thus increase the chances of a breach).
Where can MalwareBytes Make Improvements?
Over the years that I’ve been using MalwareBytes, here are some of the things that I’ve identified that they may be able to improve upon.
Low Systematic Lab Scores
It’s difficult to tell how accurate and indicative the lab tests you see in the literature that compares the various antivirus and anti-malware products on the market.
For example, some established companies may be able to optimize their detection algorithms to look better against what they know about these tests so as to look better to consumers looking to use these lab scores as an independent way of evaluating performance.
To that end, MalwareBytes is apparently a newcomer to such lab tests, and perhaps their database or approach may not be as optimized to perform better. Nevertheless, the scores undermine my confidence in the product because I’m left wondering why the low scores.
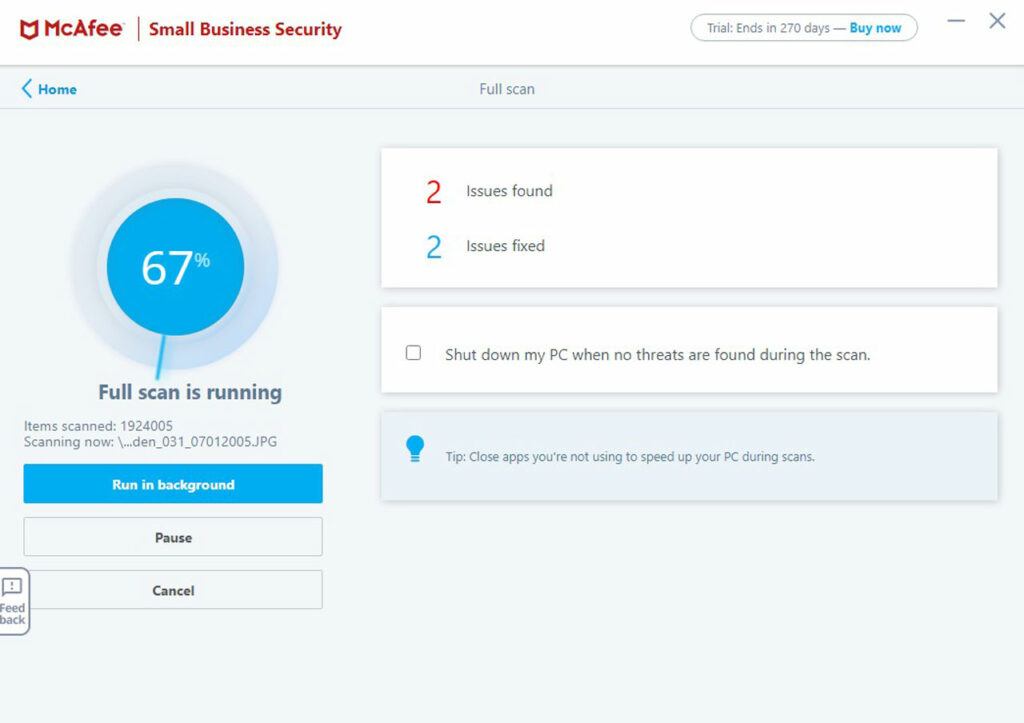
On the other hand, I have noticed in recent years that MalwareBytes hasn’t caught files that say McAfee Antivirus has caught. That said, it’s not clear to me if the antivirus program detected a legitimate virus or it was just overzealous on something that only appeared to be harmful but wasn’t.
Moreover, labs can test for known malware or emulated ones from the past, but it may not be great at evaluating emerging threats (which is what most of us have to face since cybercriminals will always find the next thing to exploit and not revert to what is already known).
Auto Update Prone to Failing
I’ve had an instance where MalwareBytes suddenly disappeared from my computer. Upon further digging, I realized that on one of the automatic updates of the software, it didn’t finish for some reason.
Therefore, I had to re-download the software, and then re-install it. As I did so, I also had to coerce the installer to get past aborted reinstall attempts as it kept insisting an install was already in progress (i.e. the failed one).
Eventually, I got it to work, but it was an annoyance that caused me to be without this software for the time that I didn’t even realize I was missing its protection!
VPN Can Be Flaky
I’ve had instances where the MalwareBytes Privacy VPN suddenly quits working on me and either reverts back to non-VPN connection or kills my internet altogether (where I have to disable MalwareBytes Privacy to restore it).
Granted, this had happened more frequently when I first started using it, but it has happened less frequently as time went on. So perhaps they’re still actively working to improve this product.
That said, when my wife and daughter complain that there’s no internet on their machines, usually the first thing I tell them to do is to disable the MalwareBytes Privacy VPN, and that usually does the trick. So indeed, this is certainly something they can improve upon.
Final Thoughts / Conclusion
MalwareBytes has been my primary endpoint security program since June 2016. I personally have been pretty satisfied with its performance over the years though I realize that I can’t rest on my laurels when it comes to cybersecurity.
Come to think of it, cybersecurity (let alone anti-malware and antivirus included) is never going to be 100% because there’s a tradeoff between resource utilization, speed, and accuracy. I’ve had a case where established antivirus software like McAfee and Kapersky had missed stuff that MalwareBytes caught and vice versa.
The bottom line is that I had to think of MalwareBytes (and antimalware software in general) as merely another layer of defense in the overall security posture of my computer and ultimately my home.
Indeed, I’d much rather exercise good security practices like not clicking on suspect links, avoiding suspect email attachments, using a VPN, being situationally aware of identity theft, and using strong passwords. And then let MalwareBytes supplement the good security practices.
I don’t think it’s a good idea to use the software as a catch-all when I’m not doing my part to prevent bad things from happening that are within my power.
Yet I recognize that nobody’s perfect (you never know if a child or wife or even myself accidentally clicks on something we shouldn’t have), and so MalwareBytes is more or less my insurance policy to bail me out should such a calamity occur. Again, with cybersecurity and cybercrime being an ever evolving game of cat-and-mouse, nothing is going to prevent all malware from getting through. That’s why no software is a substitute for doing your due diligence to minimize your exposure in the first place before letting that software help get you out of trouble should it happen!